For the past 2 weeks I’ve been receiving notifications reporting that one of my clients SBS 2008 environments is about to have some Exchange certificates expire.
Please Note, I provide Small Business Server consulting services, more information is available here!
Below is an example of the event log:
Source: MSExchangeTransport
Category: TransportService
Event ID: 12017
User (If Applicable): N/A
Computer: server.domain.local Event Description: An internal transport certificate will expire soon. Thumbprint:ZOMGZOMGZOMGZAOMGZOMGZOMGZOM, hours remaining: 46 Event Log Name: Application Event Log Type: warning Event Log Date Time: 2012-03-08 13:15:36
Now upon initial research, apparently we were supposed to just be able to run the “Fix My Network” wizard inside of the SBS Console. Running this during the warnings, and after the certificate actually expired did absolutely nothing. The wizard was unable to detect the certificate had expired. It did report something to do with issues with an SMTP connector, however everything was working, and when trying to fix that, the wizard errored out and could not complete. I also read another article that running the “Setup my internet address” my fix the issue, but however it did not.
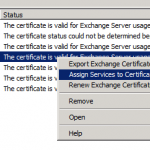
I decided to take a look at all the certificates currently install and also in use. To view the certificates installed, go to “Start”, then “Run”, type in “mmc.exe” and hit OK. Click on “File”, then “Add/Remove Snap-in”. Inside of this window, highlight “Certificates” and move to the right (hit the button with the arrow). Another window should open, select “Computer Account”, and follow through with the wizard. Once the certificates open, expand “Personal” and “Certificates” underneath it.
In my environment I noticed that there were two certificates that were identical, only difference being expiration. I had a feeling that the proper certificate existed on the server, however for some reason it was using an older one that it should not be. Keep in mind, this specific server was migrated from another (SBS 2008 to SBS 2008 Migration to new hardware).
To confirm they were identical, I opened up a Exchange Shell (find it in the start menu, and right click and “Run As Administrator”). I typed in “Get-ExchangeCertificate | FL”. The output confirmed that the certificates were the same and performed the same function.
ONLY PERFORM THIS if exchange is using the wrong certificate and you have two certificates which are the same, only with different expiration dates. If you do not, you are experiencing another problem and these instruction either won’t help you, or make your problem worse.
I decided to switch Exchange over to the new certificate:
1) Get the thumbprint of the newer certificate, it will be provided when you run “Get-ExchangeCertificate | FL”. Make sure the services and information match the certificate that is about to expire.
2) With the Exchange Shell still open type in “Enable-ExchangeCertificate thumbprint -Services SMTP,POP,IMAP” (sub in the thumbprint where it says thumbprint).
3) It will ask you to confirm, click ok.
4) Delete the old certificate, but make sure you back it up first. Export the old expiring certificate using the Certificate view inside of mmc.exe (what we did above). Export it (with extended data) so it can easily be re-imported if any issues occur. If you do need to restore it, inside of the Certificate view in mmc.exe, simply right click, re-import, and use the “Enable-ExchangeCertificate” (shown above) to re-activate it.
Hope this helps!