When you’re looking for additional or enhanced options to secure you’re business and enterprise IT systems, MFA/2FA can help you achieve this. Get away from the traditional single password, and implement additional means of authentication! MFA provides a great compliment to your cyber-security policies.
My company, Digitally Accurate Inc, has been using the Duo Security‘s MFA product in our own infrastructure, as well as our customers environments for some time. Digitally Accurate is a DUO Partner and can provide DUO MFA Services including licensing/software and the hardware tokens (Duo D-100 Tokens using HOTP).
What is MFA/2FA
MFA is short for Multi Factor authentication, additionally 2FA is short for Two Factor Authentication. While they are somewhat the same, multi means many, and 2 means two. Additional security is provided with both, since it provides more means of authentication.
Traditionally, users authenticate with 1 (one) level of authentication: their password. In simple terms MFA/2FA in addition to a password, provides a 2nd method of authentication and identity validation. By requiring users to authentication with a 2nd mechanism, this provides enhanced security.
Why use MFA/2FA
In a large portion of security breaches, we see users passwords become compromised. This can happen during a phishing attack, virus, keylogger, or other ways. Once a malicious user or bot has a users credentials (username and password), they can access resources available to that user.
By implementing a 2nd level of authentication, even if a users password becomes compromised, the real (or malicious user) must pass a 2nd authentication check. While this is easy for the real user, in most cases it’s nearly impossible for a malicious user. If a password get’s compromised, nothing can be accessed as it requires a 2nd level of authentication. If this 2nd method is a cell phone or hardware token, a malicious user won’t be ale to access the users resources unless they steal the cell phone, or hardware token.
How does MFA/2FA work
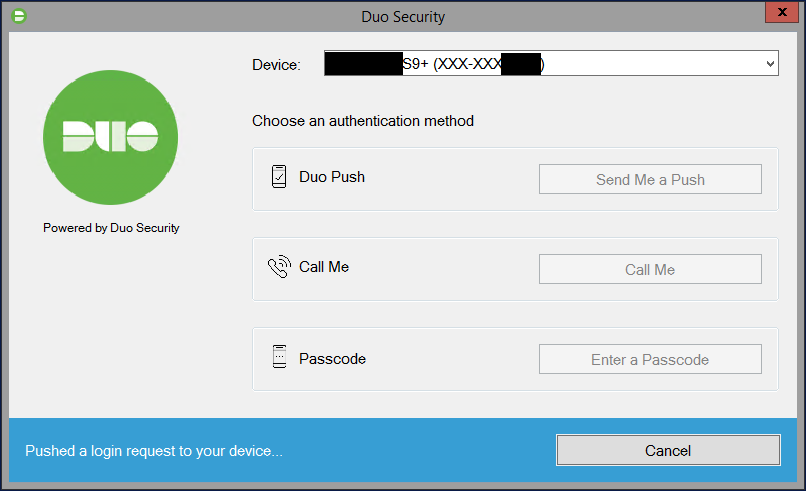
When deploying MFA or 2FA you have the option of using an app, hardware token (fob), or phone verification to perform the additional authentication check.
After a user attempts to logs on to a computer or service with their username and password, the 2nd level of authentication will be presented, and must pass in order for the login request to succeed.
Please see below for an example of 2FA selection screen after a successful username and password:
After selecting an authentication method for MFA or 2FA, you can use the following
2FA with App (Duo Push)
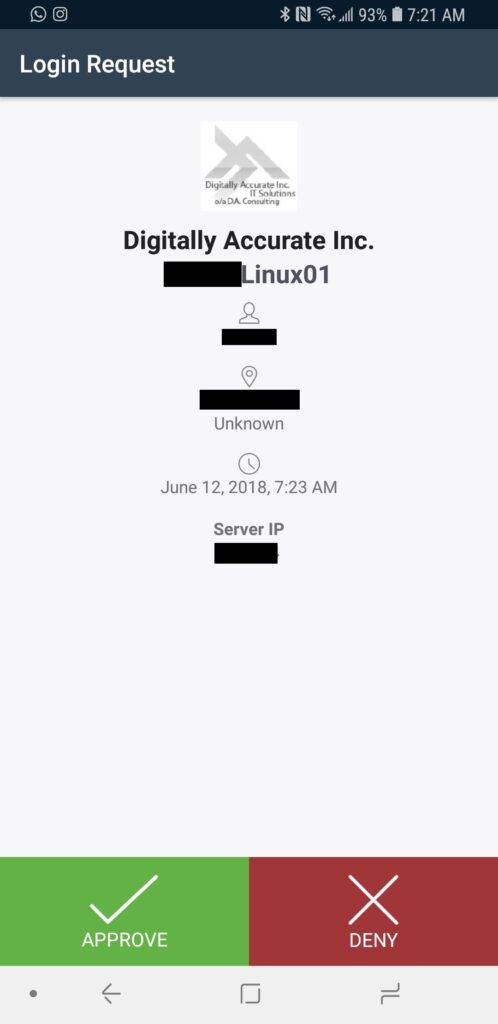
Duo Push sends an authentication challenge to your mobile device which a user can then approve or deny.
Please see below for an example of Duo Push:
Once the user selects to approve or deny the login request, the original login will either be approved or denied. We often see this as being the preferred MFA/2FA method.
2FA with phone verification (Call Me)
Duo phone verification (Call Me) will call you on your phone number (pre-configured by your IT staff) and challenge you to either hangup to deny the login request, or press a button on the keypad to accept the login request.
While we rarely use this option, it is handy to have as a backup method.
2FA with Hardware Token (Passcode)
Duo Passcode challenges are handled using a hardware token (or you can generate a passcode using the Duo App). Once you select this method, you will be prompted to enter the passcode to complete the 2FA authentication challenge. If you enter the correct passcode, the login will be accepted.
Here is a Duo D-100 Token that uses HOTP (HMAC-based One Time Password):
When you press the green button, a passcode will be temporarily displayed on the LCD display which you can use to complete the passcode challenge.
You can purchase Hardware Token’s directly from Digitally Accurate Inc by contacting us, your existing Duo Partner, or from Duo directly. Duo is also compatible with other 3rd party hardware tokens that use HOTP and TOTP.
2FA with U2F
While you can’t visibly see the option for U2F, you can use U2F as an MFA or 2FA authentication challenge. This includes devices like a Yubikey from Yubico, which plugs in to the USB port of your computer. You can attach a Yubikey to your key chain, and bring it around with you. The Yubikey simply plugs in to your USB port and has a button that you press when you want to authenticate.
When the 2FA window pops up, simply hit the button and your Yubikey will complete the MFA/2FA challange.
What can MFA/2FA protect
Duo MFA supports numerous cloud and on-premise applications, services, protocols, and technologies. While the list is very large (full list available at https://duo.com/product/every-application), we regularly deploy and use Duo Security for the following configurations.
Windows Logins (Server and Workstation Logon)
Duo MFA can be deployed to not only protect your Windows Servers and Workstations, but also your remote access system as well.
When logging on to a Windows Server or Windows Workstation, a user will be presented with the following screen for 2FA authentication:
Below you can see a video demonstration of DUO on Windows Login.
DUO works with both Windows Logins and RDP (Remote Desktop Protocol) Logins.
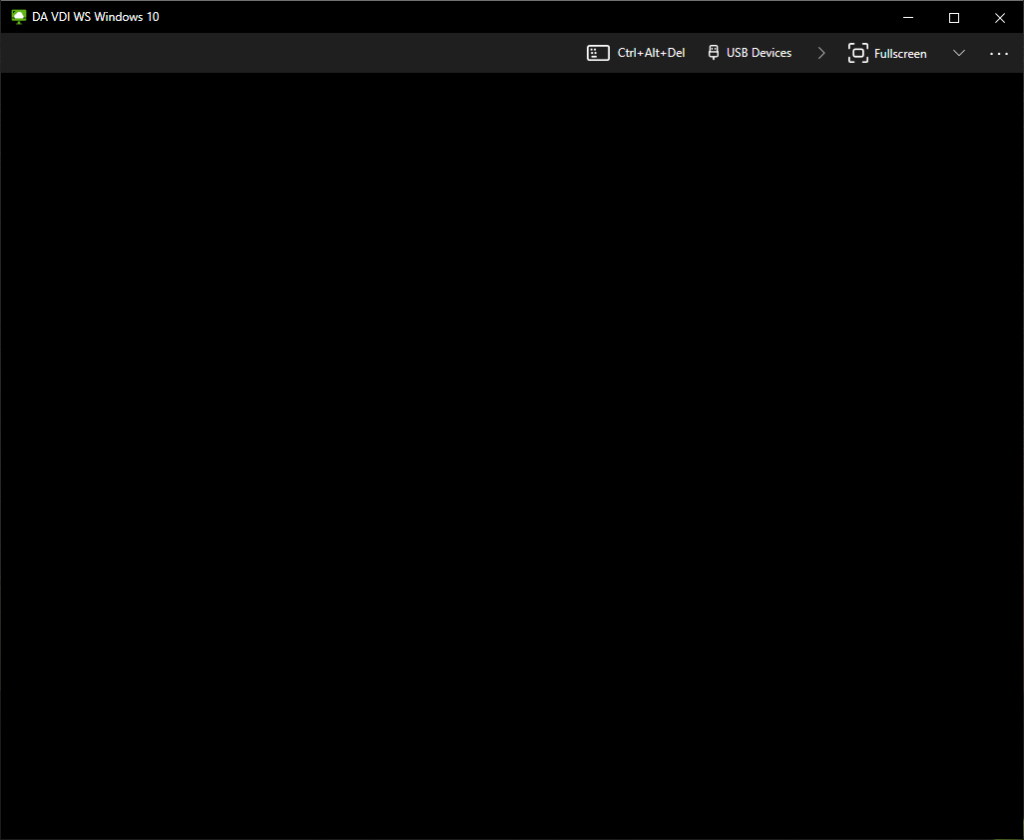
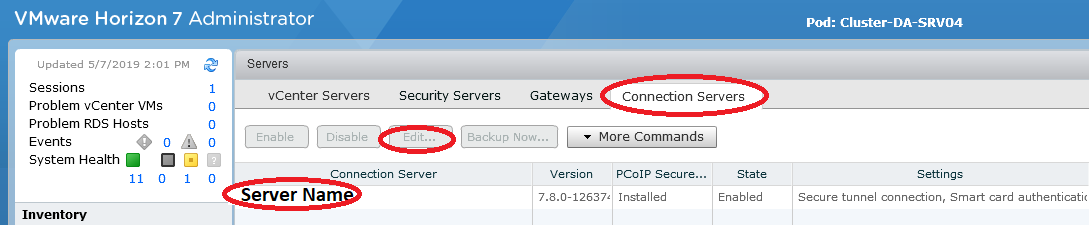
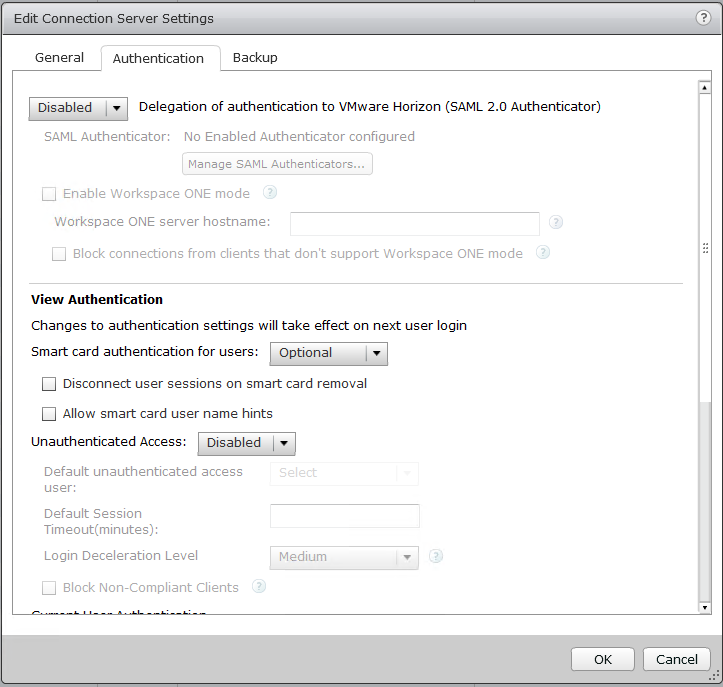
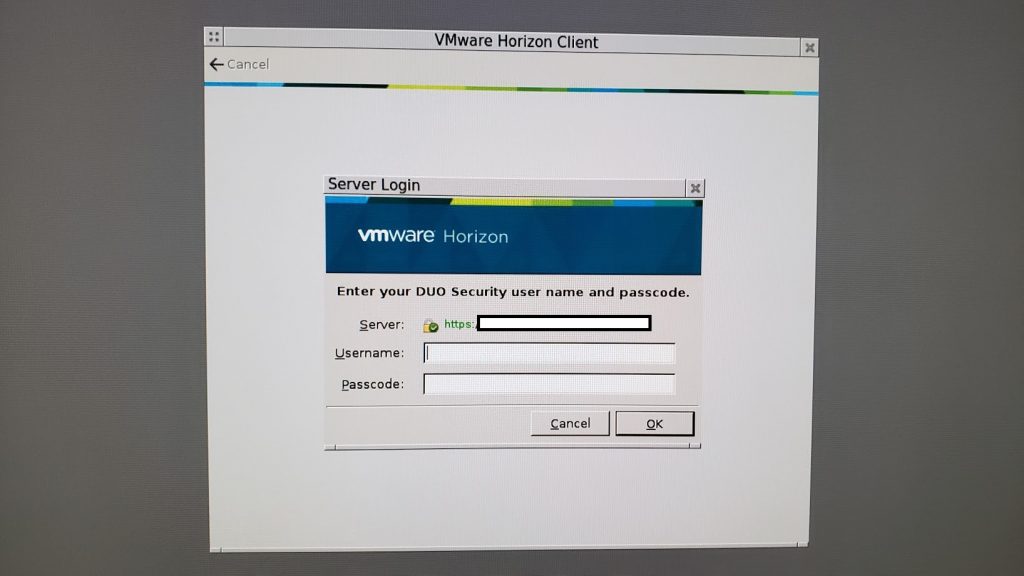
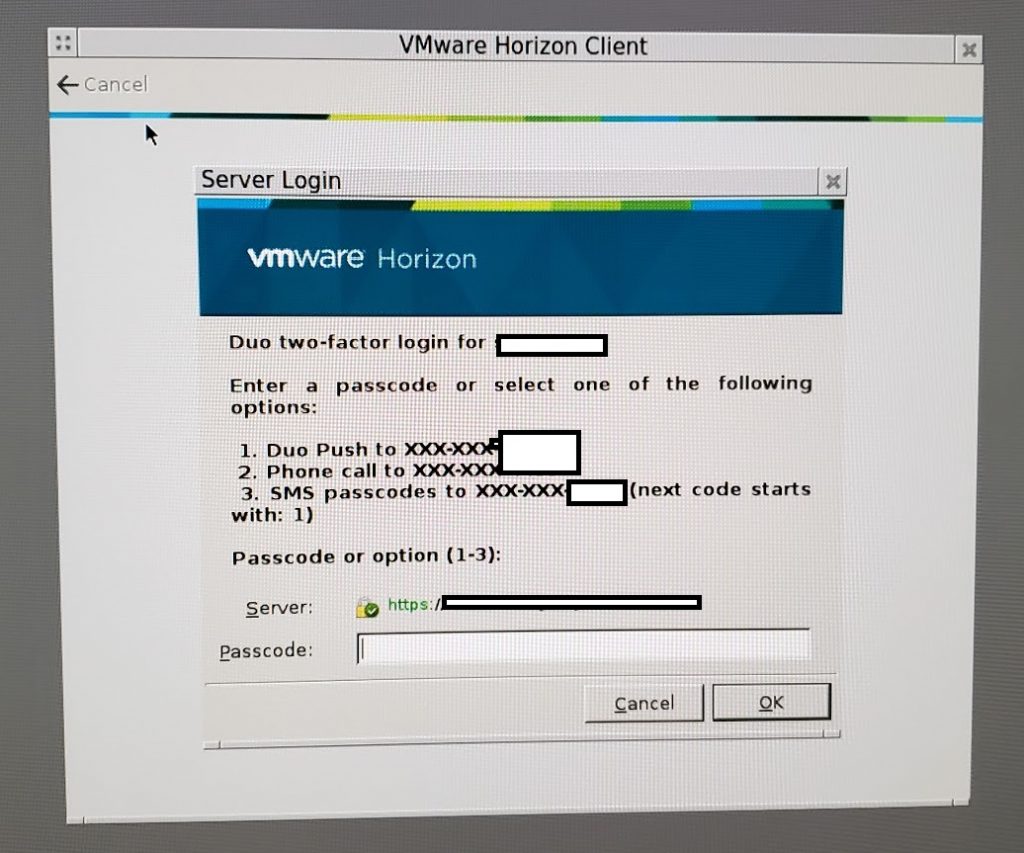
VMWare Horizon View Clients (VMWare VDI Logon)
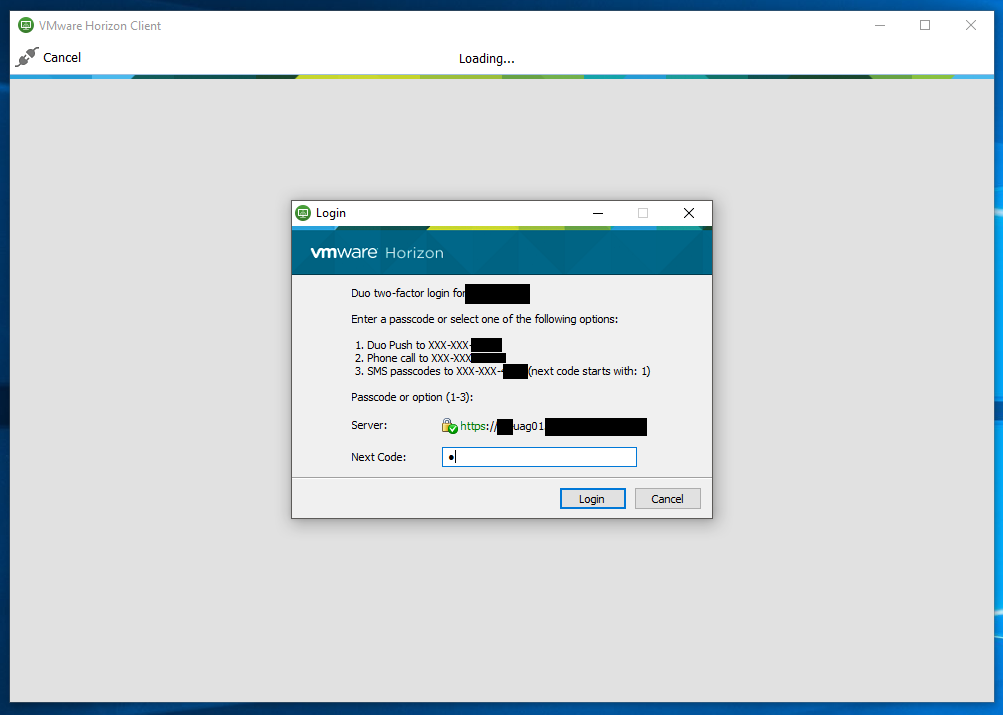
Duo MFA can be deployed to protect your VDI (Virtual Desktop Infrastructure) by requiring MFA or 2FA when users log in to access their desktops.
When logging on to the VMware Horizon Client, a user will be presented with the following screen for 2FA authentication:
Below you can see a video demonstration of DUO on VMware Horizon View (VDI) Login.
Sophos UTM (Admin and User Portal Logon)
Duo MFA can be deployed to protect your Sophos UTM firewall. You can protect the admin account, as well as user accounts when accessing the user portal.
If you’re using the VPN functionality on the Sophos UTM, you can also protect VPN logins with Duo MFA.
Unix and Linux (Server and Workstation Logon)
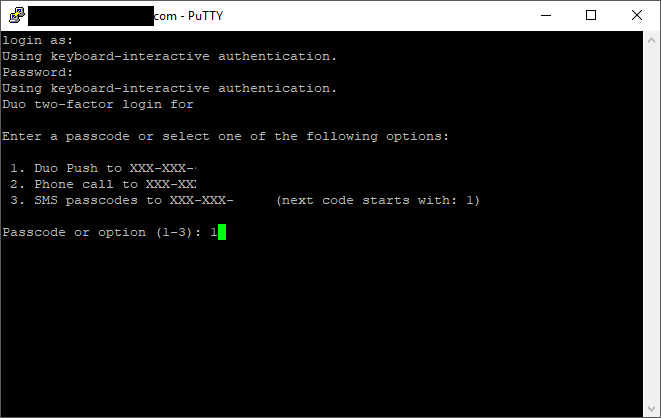
Duo MFA can be deployed to protect your Unix and Linux Servers. You can protect all user accounts, including the root user.
We regularly deploy this with Fedora and CentOS (even FreePBX) and you can protect both SSH and/or console logins.
When logging on to a Unix or Linux server, a user will be presented with the following screen for 2FA authentication:
Below you can see a video demonstration of DUO on Linux.
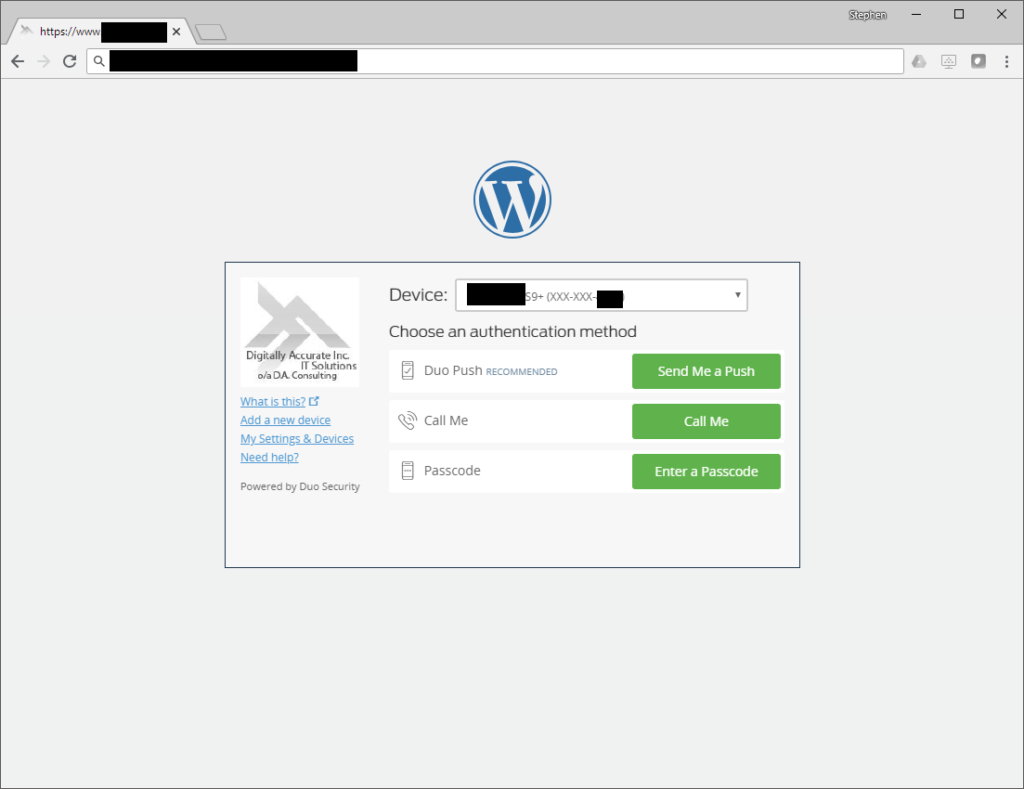
WordPress Logon
Duo MFA can be deployed to protect your WordPress blog. You can protect your admin and other user accounts.
If you have a popular blog, you know how often bots are attempting to hack and brute force your passwords. If by chance your admin password becomes compromised, using MFA or 2FA can protect your site.
When logging on to a WordPress blog admin interface, a user will be presented with the following screen for 2FA authentication:
Below you can see a video demonstration of DUO on a WordPress blog.
How easy is it to implement
Implementing Duo MFA is very easy and works with your existing IT Infrastructure. It can easily be setup, configured, and maintained on your existing servers, workstations, and network devices.
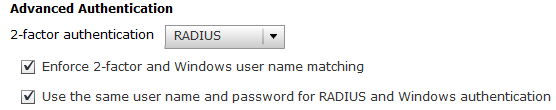
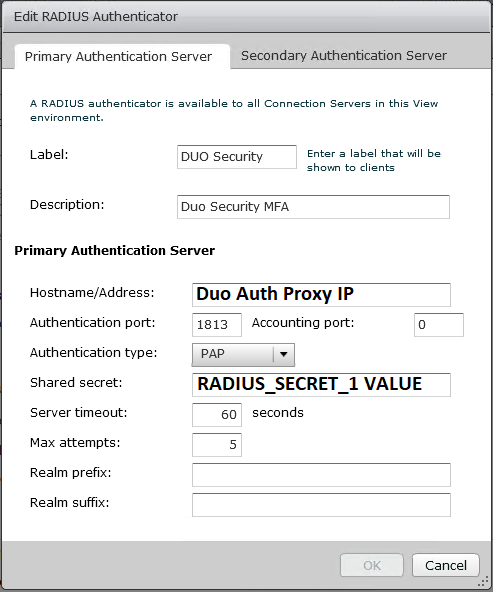
Duo offers numerous plugins (for windows), as well as options for RADIUS type authentication mechanisms, and other types of authentication.
How easy is it to manage
Duo is managed through the Duo Security web portal. Your IT admins can manage users, MFA devices, tokens, and secured applications via the web interface. You can also deploy appliances that allow users to manage, provision, and add their MFA devices and settings.
Duo also integrates with Active Directory to make managing and maintaining users easy and fairly automated.
Let’s get started with Duo MFA
Want to protect your business with MFA? Give me a call today!