Windows Server Core (on Windows Server 2019) is a great way to reduce the performance and security footprint of your servers. The operating system itself is minimalist and provides no GUI except for a command prompt, and some basic windows and tools.
All administration on Server Core must be performed via the command prompt, powershell, or remote administration tools (such as Server Manager, or the new Windows Admin Center.
Server Core provides a fantastic foundation for Windows Server Roles (roles that are integrated in the operating system), and can be installed with ease, managed remotely, and managed easily. It’s also nice too because you can allocate less CPU and RAM to virtual machines running Windows Server Core.
Getting started may be a bit tricky as you might need to learn and verse yourself with some commands, powershell, and remote management kung-fu, but overtime it’s easy!
Why WSUS?
I think I can speak for most admins out there when I say that a WSUS deployment typically consists of a single VM, with the WSUS, IIS, and WID roles installed.
WSUS is usually CPU and RAM intensive (when doing synchronizations), requires disk space, and doesn’t do much else. Because of the spikes, we usually keep this VM separate and don’t mix it with other LoBs or roles, with the exception of perhaps a file server.
Whether or not your VM runs WSUS alone, or also as a file server, since both of these roles are “Windows Roles and Features”, they are perfect to deploy on a Windows Server Core install.
There should be little administrative requirement on the WSUS server, other than re-indexing scripts, and cleanup scripts which can easily be ran from the command prompt, and the occasional Windows Update that will be installed.
Because you don’t require any 3rd party software, management consoles, or GUI related elements, it’s perfect for Server Core. By skipping on the GUI and applications, you’ll be able to allocate that memory, for WSUS/IIS itself.
How to Install and Configure WSUS on Windows Server Core
- Install Windows Server 2019 – Server Core
- Configure Network, Join to Domain, Update, etc.
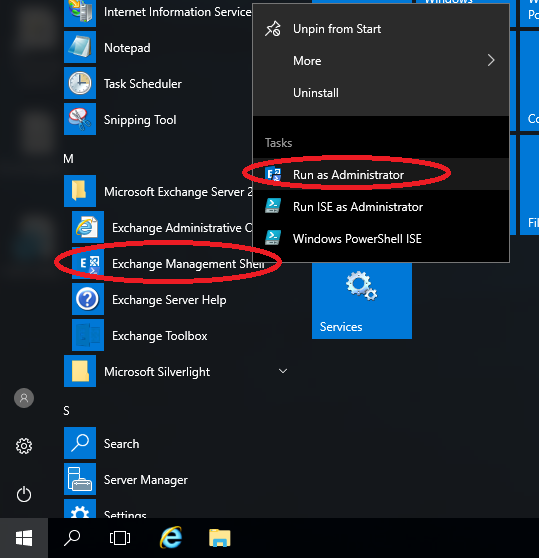
- Open “powershell” (by typing powershell) and Install the WSUS Role with the following command:
Install-WindowsFeature UpdateServices -Restart
- Exit powershell with “exit” and run the post installation task command in command prompt to configure WSUS:
"C:\Program Files\Update Services\Tools\wsusutil.exe" postinstall CONTENT_DIR=C:\WSUS
- AT THIS POINT DO NOT CONTINUE CONFIGURING WSUS AS YOU MUST APPLY A MEMORY FIX TO IIS.
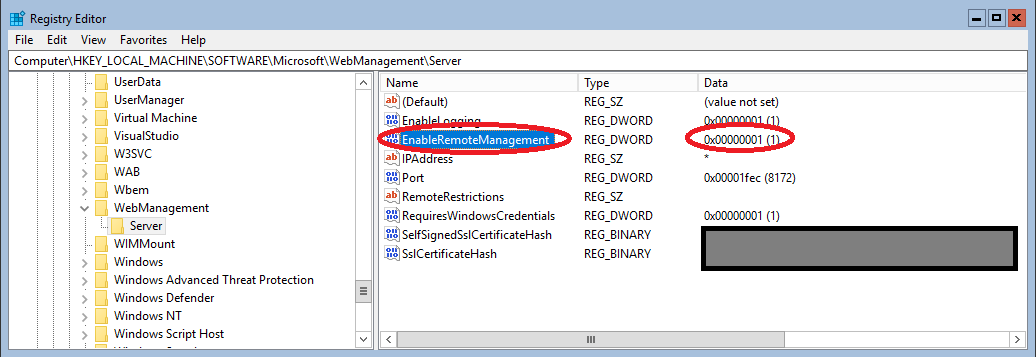
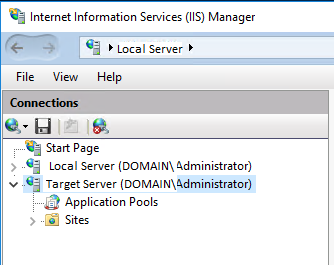
- Enable Remote IIS Management to manage and modify IIS config (to apply the memory fix below), as provided here: https://www.stephenwagner.com/2019/05/14/manage-remotely-iis-on-windows-server-2019-server-core/
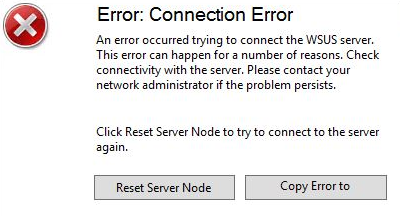
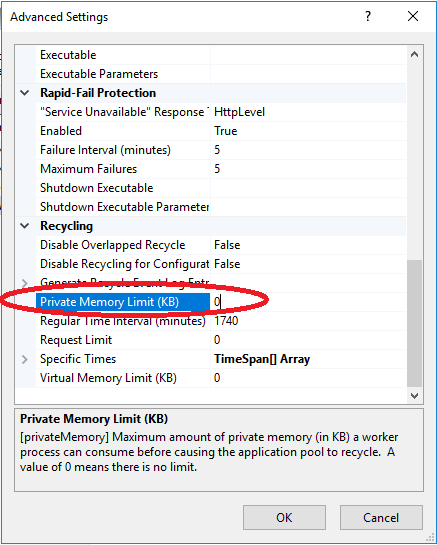
- Apply “Private Memory Limit (KB)” fix as provided here: https://www.stephenwagner.com/2019/05/14/wsus-iis-memory-issue-error-connection-error/
- Install the “Windows Server Update Services” mmc applet which is included in the Windows 10 RSAT tools. Instructions to install the RSAT are provided here: https://www.stephenwagner.com/2018/10/05/windows-10-1809-october-update-rsat/
- Open the WSUS MMC on a server or workstation on the network and connect it to the WSUS instance on your Server Core install.
- Run through the wizard as you would normally and perform an synchronization.
- Modify your GPO to point your servers and workstations towards your WSUS server.
- Enable Windows Update “Features on Demand” and “Turn Windows features on or off” via GPO as provided here:
https://www.stephenwagner.com/2018/10/08/enable-windows-update-features-on-demand-and-turn-windows-features-on-or-off-in-wsus-environments/ - Install the “sqlcmd” command so you can regularly run the WSUS re-index script, as provided here: https://www.stephenwagner.com/2019/05/14/run-wsus-cleanup-index-script-windows-server-core-without-sql-management-studio/
You’re done!
Don’t forget to regularly re-index your WSUS database and perform the routine maintenance!
Tips n Tricks
- Need to view, modify, cut/paste, or delete files and folders? Open up notepad from the command prompt to get a simple GUI where you can do this.
- CTRL + SHIFT + ESC will open a Task Manager to monitor the Server Core install
- You can use “Server Manager” remotely to manage the Server Core install after you’ve enabled it inside of “sconfig”.