So you’ve purchased some Ubiquiti UniFi hardware… You have configured it, possibly even changed your management VLAN. Now it’s time to get production ready.
When you start getting in to complicated setups with VLANs, multiple subnets, etc… Planning your UniFi deployment can get tricky.
I’ve had numerous readers reach out after reading my Ubiquiti UniFi Review and ask questions about their UniFi adoption issues, as well as what the best method is.
I regularly see IT professionals adopting via SSH or the mobile app, however in best practice and large deployments you want this to be automated and require as little human intervention as possible.
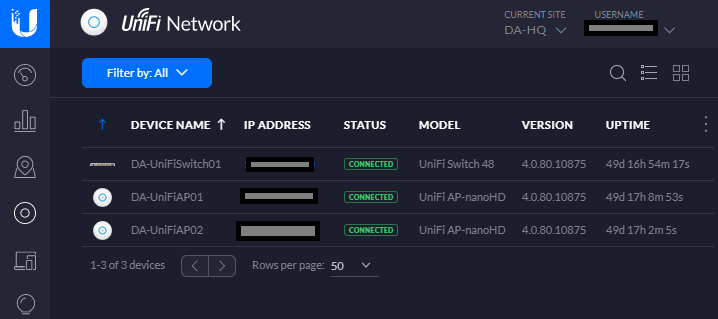
All an IT administrator should have to do is connect the device to the network and see it in the UniFi Controller. This should apply to the most simplistic, as well as the most advanced deployments.
Design
If you’re using multiple subnets and multiple VLANs, you need to make sure that when a new UniFi device (such as an Access Point or Switch) is connected, that the following two things occur:
- It can get an IP address from a DHCP Server
- It can reach out to a UniFi controller (we’ll get in to this more in a bit)
In more complicated environments, your UniFi controller may be sitting on a different VLAN and you may also have your management VLAN on a different VLAN as well (where your UniFi devices reside after adoption).
My Environment
In my environment, the following is true:
- No devices except a DHCP/DNS server and firewall/router sit on the untagged VLAN of 1.
- My UniFi devices (including controller, Access Points, and switches) have a separate dedicated management VLAN.
The purpose of having an untagged VLAN of 1 is to allow provisioning of devices that self or auto provision. This network is an isolated network that is heavily controlled via the router and firewall that is running IPS (Intrusion Prevention System) and strict firewall rules.
Normally I wouldn’t even have anything on the untagged VLAN of 1, however a provisioning network is needed. For example when you plug in a UniFi NanoHD, or a UniFi Switch, it’ll grab an IP on the untagged VLAN of 1, and look for a controller to present itself to for adoption.
Best Adoption Method
No matter how simple or complex the environment is I always recommend using the DNS method of adoption.
Most networks have DHCP and DNS, whether it’s for workstations, servers, or IT infrastructure. It’s extremely easy to setup a DNS Host (A) record or an Alias (CNAME) record of “unifi” and have it point to your UniFi Controller.
If you’re using multiple VLANs and subnets, your network must be fully routable from the untagged VLAN of 1, all the way to your UniFi controller.
I highly recommend putting strict firewall rules in place to only allow communication to the UniFi Controller from the untagged VLAN 1.
Conclusion
Following these practices allow you to simplify your UniFi deployment even on extremely large and complex networks, while not straying from keeping your network secure!
Everything is automated, efficient, and ready to use!
Leave a comment and leave me some feedback!