When deploying the Sophos XG Firewall on to Microsoft Azure, it seems as if you always need to create a new resource group and are limited to certain regions. This is not the case.
This is true when using the “Sophos XG Firewall on Microsoft Azure” quick start guide here, and/or when using the Microsoft Azure Marketplace. If you attempt to deploy to an existing Resource Group, it will prevent you from doing so. It may also restrict you from using some configurations and virtual machine sizes, and also limit which region you can deploy to.
If you’re like me and already have Infrastructure in Microsoft’s Cloud and want more control over configuration and deployment, then your’re probably looking at deploying in to an existing Resource Group, using a more customized configuration, and may have the requirement to deploy to other Azure regions. See below for my own “Quick start to customized Sophos XG deployments on Microsoft Azure” guide.
Also, another interesting note is that the Sophos XG firewalls on Azure do not support the Microsoft Azure backup features. Since you cannot use the Azure backup features on Azure for the Sophos XG firewalls, you’ll need to use the internal Sophos XG configuration backup function. Once configured, you’ll need to be aware of how to deploy a new XG instance (in to an existing Resource Group) in the event of a failure. If a catastrophic failure does occur, you’ll need to re-provision a new Sophos XG instance on Azure, and then restore the Sophos XG configuration to the VM.
Sophos has alternative methods for deploying to Azure, however they are difficult to find. I actually had to spend quite a bit of time to find information, and then spent tons of time learning how to deploy it properly as well. Sophos has GitHub configured as a repo for their Azure XG deployment templates, along with some other goodies that may come in handy. The URL for their GitHub site is https://github.com/sophos-iaas/xg-azure
Before we begin, we make the following assumptions:
- You are knowledgeable and skilled with Microsoft Azure
- You are familiar with deploying VMs and objects to Microsoft Azure
- You have already configured a resource group and/or have existing objects deployed
- You have already configured subnets for your Sophos XG (Internal and WAN facing)
How to deploy Sophos XG Firewall on Microsoft Azure to existing Resource Group in any region.
Now let’s get started. Here’s my Quick start guide to customized Sophos XG deployments on Microsoft Azure (in to existing Resource Groups).
- Go to https://github.com/sophos-iaas/xg-azure and read the page. Once you’re ready to start, scroll down to “Deployment via template”, and select the button that says “Deploy to Azure”.
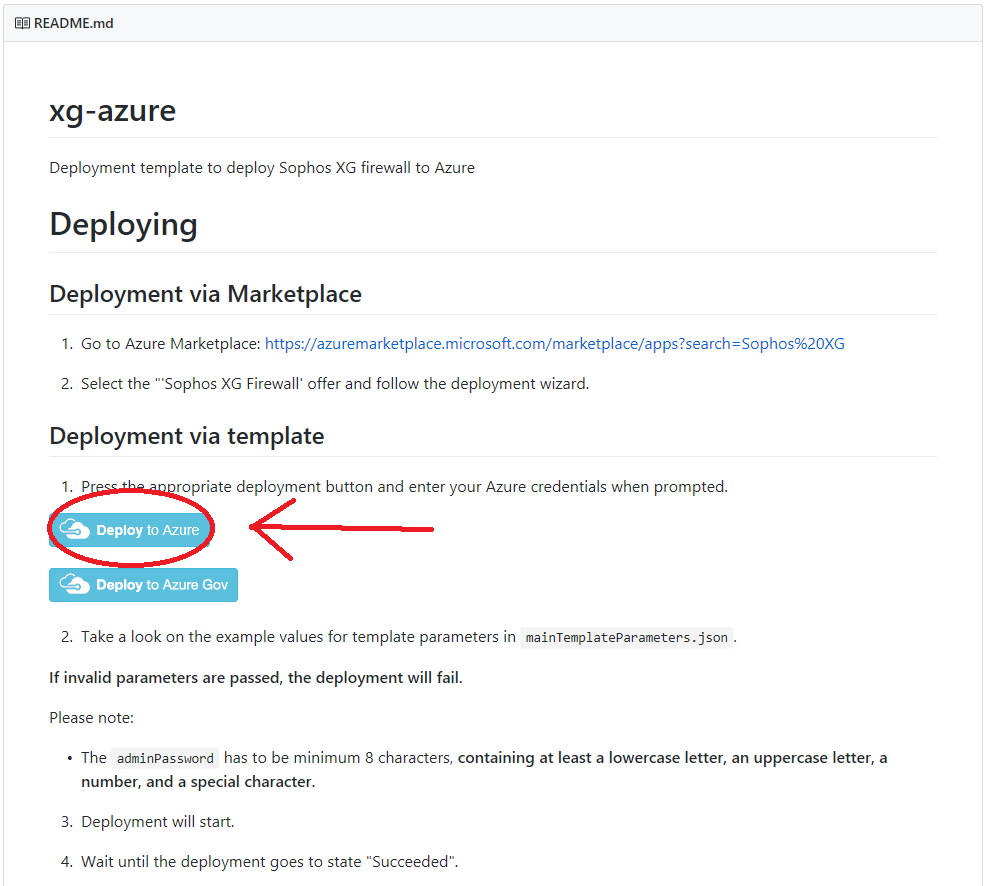
- Log in to Microsoft Azure (if you’re not already) and you’ll see the template ready to be deployed. Before filling out the fields, I would recommend looking at what fields are required, and documenting which sections you need to fill out with what details you will populate. I always record and document these settings so that if an issue ever pops up, or if I need to re deploy, I’ll have the previous settings immediately available. If you’re deploying in to an existing Resource Group, configure the fields to reflect it. To proceed with the template deployment, populate the fields, review the ToS, and continue if you accept the terms. See below for the blank template.
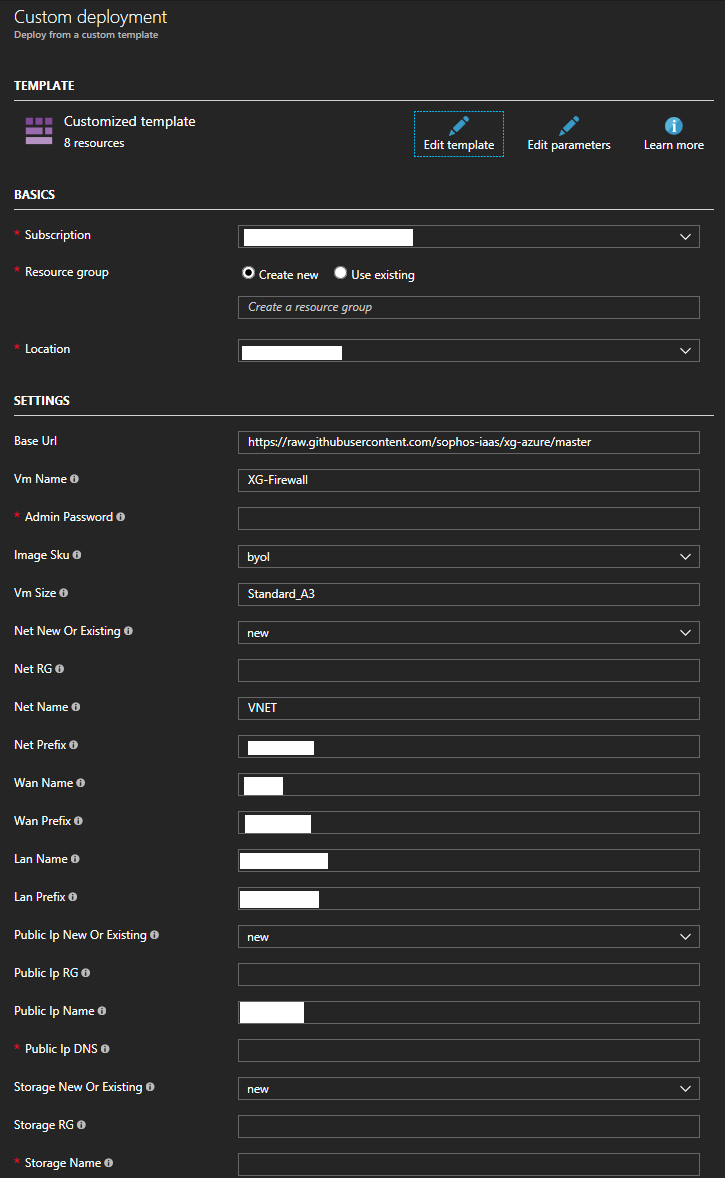
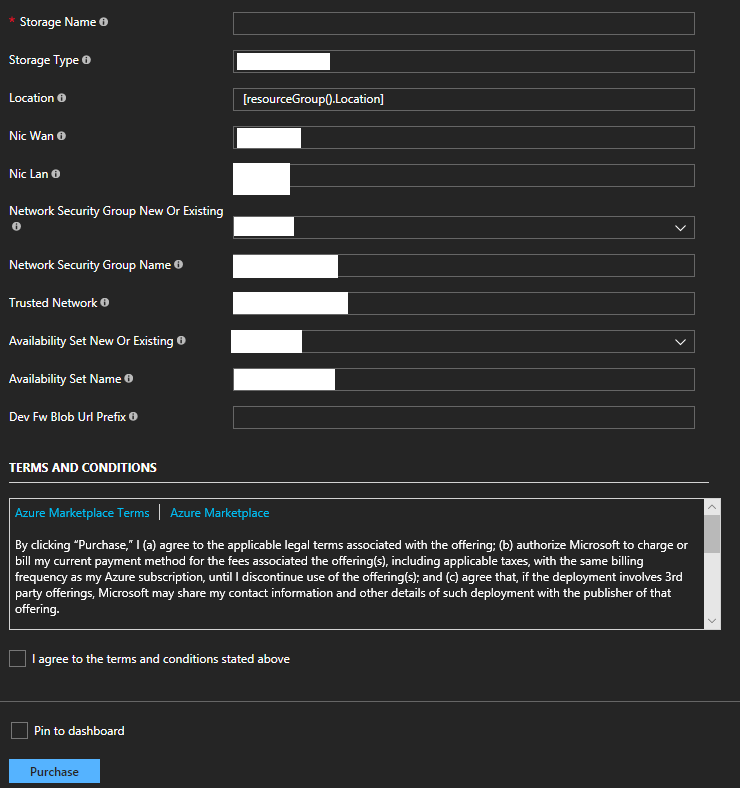
- After populating the template and executing the deployment, if all goes well you’re Sophos XG firewall should now be deployed in to your existing Resource Group. Please see below for an example of a successful deployment.
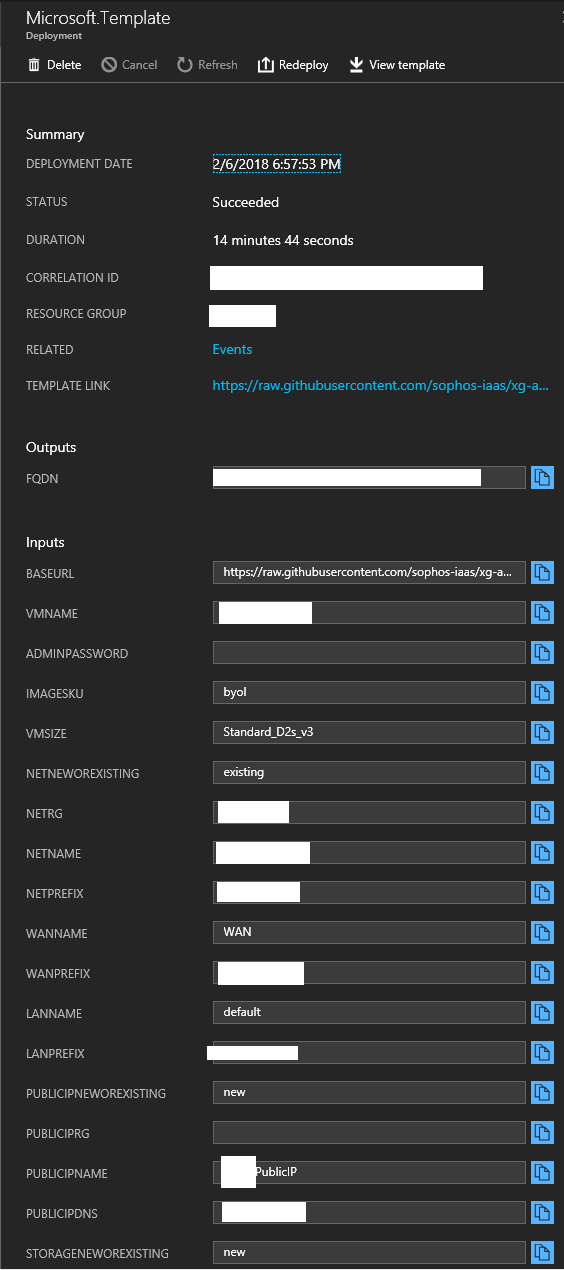
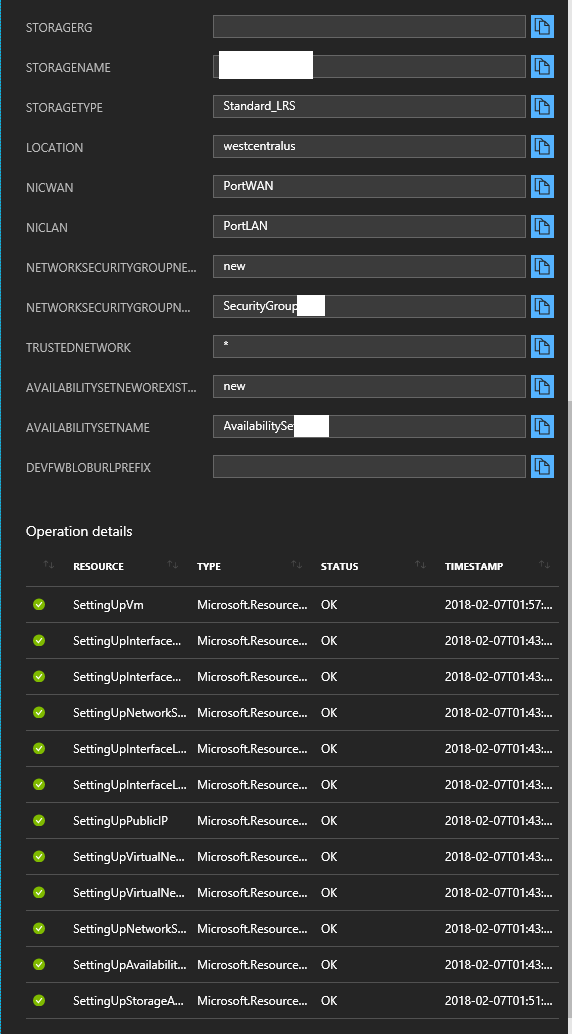
- And that is it! You can now head over to “All Resources” to view all the objects and make sure everything is configured properly. After double or triple checking your config, and checking/configuring your security groups, you can power up the VM and start playing with your new Sophos XG Firewall deployed on Microsoft Azure.
Final Thoughts
After doing all this you should be able to deploy these on the fly whenever needed. As mentioned above, this is critical knowledge for Sophos XG admins using Microsoft Azure as this process needs to be known for backup and disaster recovery purposes. Also, chances are you’ll need to attempt deployment multiple times before successfully deploying the instance. I had 4 or 5 unsuccessful deployment attempts due to various issues such as mis-typed fields, blank fields, and incorrectly populated fields, so don’t feel bad if it takes you some time. It’s a learning process!
Leave a comment and let me know how your deployment went and if you have any questions!